The Wincor Nixdorf PORT IO Driver ‘wnport.sys’ was found to have multiple stack overflow vulnerabilities.
Driver Download Link https://driverpack.io/en/hwids/ROOT%5CWNPORT
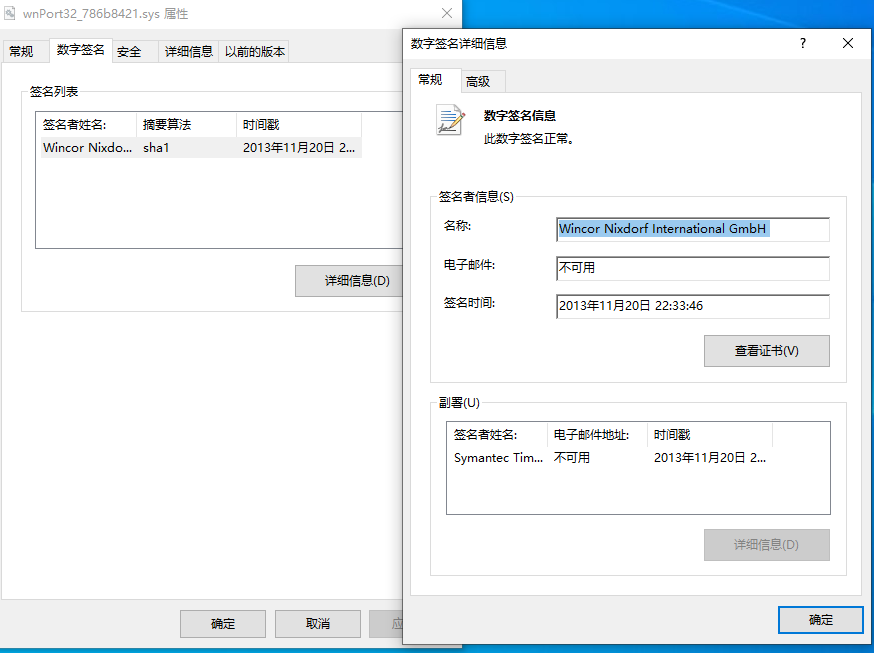
The Driver ‘s Digital Signature. though it’s has not WHQL signature. is still permitted to be loaded by the latest version of Windows. However, for drivers with valid digital signatures issued before this policy update, Windows maintains compatibility by allowing them to bypass the WHQL requirement.
Therefore, this driver may still have an impact on the new 32-bit version of Windows.
The IOCTL_DEVICEIO_CONTROL_FUNCTION subroutine at sub_11100 contains multiple IOCTL handlers that can trigger stack overflow conditions. Specifically, the following IOCTL codes are affected:
0x801020400x801020440x801020500x80102054
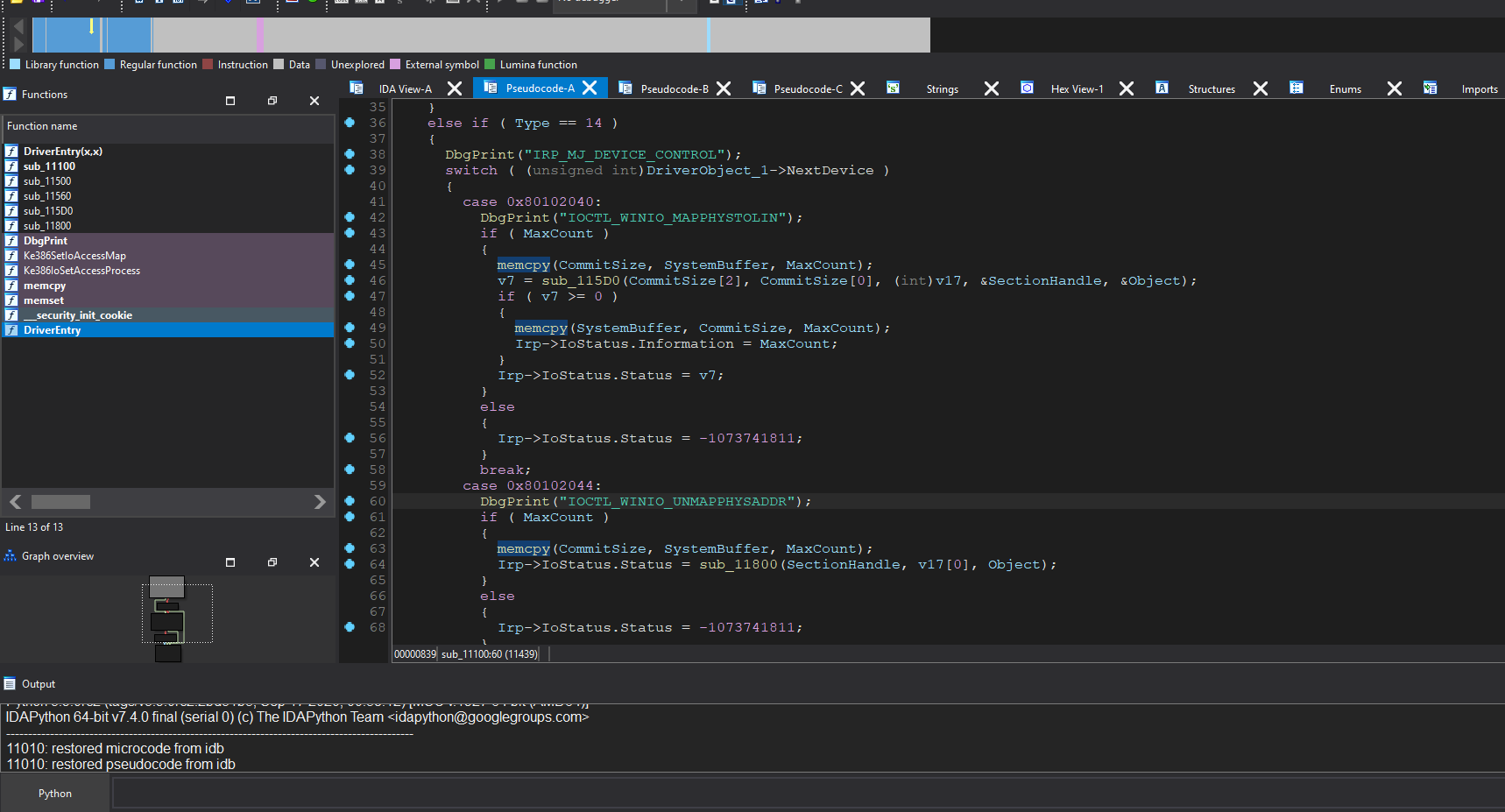
The MaxCount parameter actually represents the input buffer length, while CommitSize is constrained to a maximum of four size_t units. Consequently, a stack overflow will occur if the input buffer length exceeds the CommitSize.
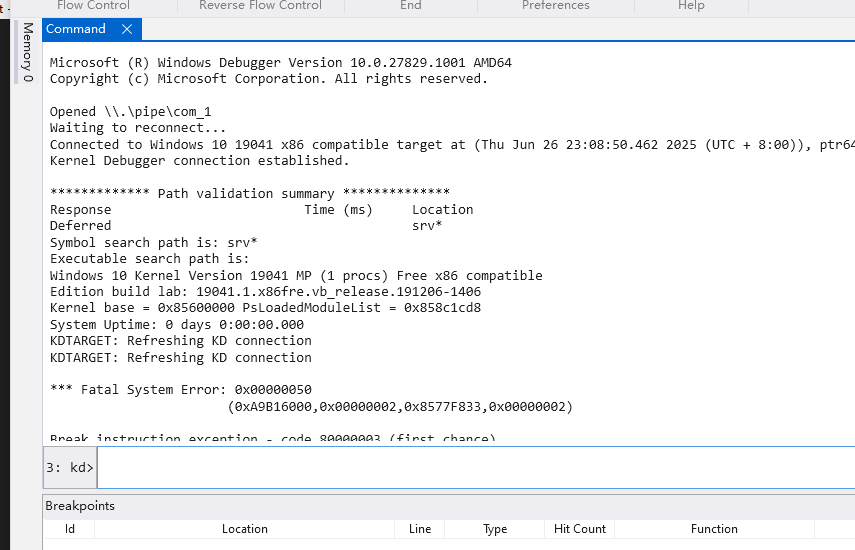
After using DeviceIoControl to send a large input buffer that exceeds the driver’s internal stack allocation , the system may encounter a stack overflow condition. This occurs because the driver’s IOCTL handler at sub_11100 processes the buffer without proper bounds checking, leading to memory corruption.
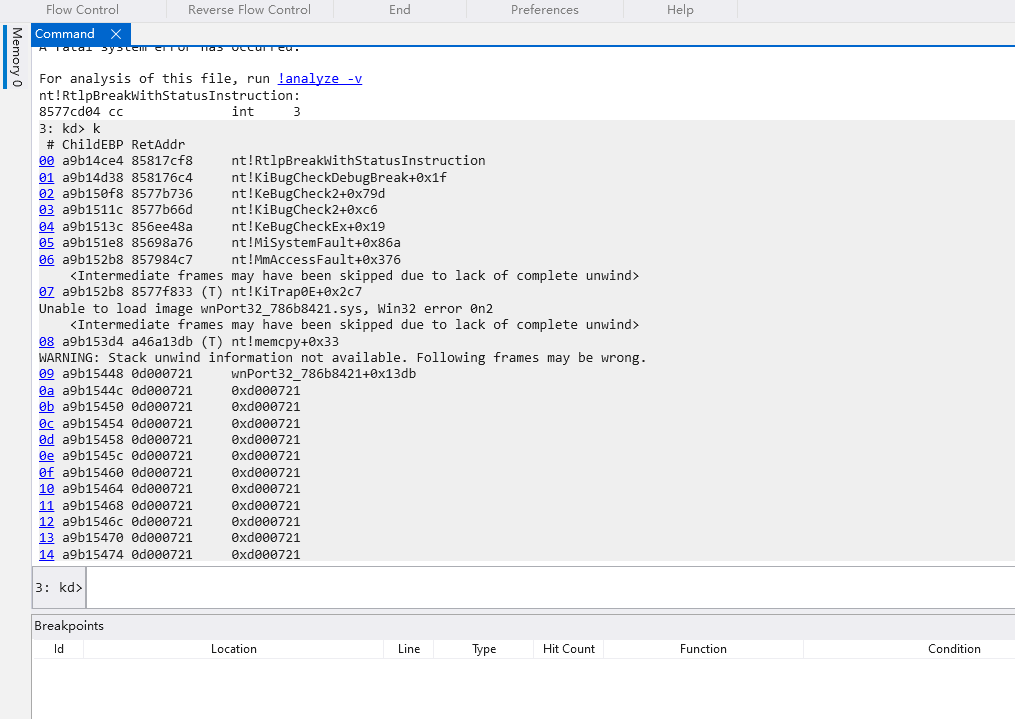
This driver has triggered a PAGE_FAULT_NON_PAGE blue screen error, resulting in the system crashing., disrupting system operation by causing improper access to non-paged memory. Beyond the immediate system crash, its vulnerabilities can lead to memory corruption, enabling malicious entities to manipulate critical memory areas. In the worst - case scenario, it allows for arbitrary code execution, giving attackers the ability to run unauthorized commands with elevated privileges. What’s more concerning is that the driver’s IOCTL functions can be called by low - privileged programs, making it easier for attackers to exploit these flaws and undermine system integrity.